Dictionaries for brute wifi are often used by professional hackers in their activities. Of course, you will also need specialized software, which is necessary for synchronization with the dictionary database.
But if the programs themselves can be easily downloaded from any open source, then you will have to look hard for good dictionaries for Brutus. Moreover, this is a rare and very valuable find on the Internet.
But if a professional understands everything without unnecessary words, then for a less experienced audience all this terminology is a novelty. The average user cannot understand why and for what purpose a brute force wifi wpa2 may be required. How to use it and what does all this “have” with?
What is Brutus
Brutus is one of the systems for cracking a password by selecting a key combination. Your computer will be able to guess the password if you have the appropriate software and a dictionary database.Brute can be used almost anywhere where the system is protected with a password. It could be Mailbox, social page or something else.
We will talk in more depth about brute access to a wifi router. Our goal is to gain access to a third-party Internet connection. And this is where dictionaries, software and patience are required.
Where does Brute Wifi begin?
Initially, it is worth distinguishing between the available router encryption systems - WPA and WPA2. In both cases, you can work with password generation, but it is the latter option for encrypting the system that is less desirable.The dictionary for Brute wifi wpa2 connects to software that automatically generates and searches for matches. This procedure is lengthy and can take at least several days. But again, this only depends on the complexity of the password itself.
But if you managed to download dictionaries from a reliable and proven database, then you can count on a positive final result.
Are all dictionaries the same?
Brushing wifi access should only be started if you clearly understand all the sequential steps and stages that you will have to overcome. The fact is that even brute wifi dictionaries are very different from each other and their use may not always be effective if you select the wrong database.Also take into account the maximum number sequence in the dictionary you downloaded. Most often, users use 8 digits in the password, but there are dictionaries with a base of password combinations of 7-9 digits.
The wifi password dictionary should be adapted to your region. That is, there are separate databases in English, Spanish, French and other languages. In our case, we need a database of Russian password combinations.
Before synchronizing dictionaries, take the time to view them in a text editor and make sure that they are compiled at the proper level and cover the majority of popular combinations.
Hacking access to wifi from the phone screen
It is quite possible to perform wifi brute force from an Android smartphone, since the corresponding software is available for free and can be downloaded without restrictions. And then after installation, you will need to use the same dictionaries, where you will probably select a unique password combination.The best dictionaries on the web
We have collected the best dictionary databases for subsequent password selection and wifi brute force. It’s easy to make sure of this - download our dictionaries to your computer and try them.The presented dictionaries have one of the largest databases of combinations of password options for Russian queries. And the dictionaries themselves are constantly being improved and supplemented, which is important for new users.
Download dictionaries for Brute WiFi (wpa, wpa2)
- :
- :
- [Dates in various spellings]:
- [Small dictionary of 9 million words]:
- [Passwords of emails leaked in 2014]:
Benefits of using Pyrit
Hacking captured handshakes is the only way cracking WPA/WPA2 passwords. It is performed using the brute force method (password search).
By the way, if you are not yet familiar with the technique of capturing handshakes, then refer to the article “”.
Since using brute force does not guarantee a positive result, several techniques have been invented that can significantly increase the chances of success. These include:
- using video cards to guess passwords (significantly increases the speed of search)
- use of tables with pre-calculated hashes (increased speed + ability to reuse for the same access point, ability to try dozens of handshakes from one access point in a matter of seconds)
- using good dictionaries (increases chances of success)
Pyrit can use all these techniques - that's why it is the fastest WPA/WPA2 password cracker, or one of the top two along with oclHashcat.
Other programs also implement these techniques. For example, both oclHashcat and coWPAtty implement dictionary search. coWPAtty implements pre-calculation of hashes (but does not support the use of graphics cards). oclHashcat allows you to use the power of video cards, but does not pre-calculate hashes. Looking ahead, I’ll note that in oclHashcat you can implement a preliminary calculation of hashes and use the obtained data repeatedly for one access point to check several handshakes without increasing the time for calculating hashes, as this will be described later. Aircrack-ng searches through the dictionary and effectively uses multi-core processors, but does not use other "accelerations".
On my system, oclHashcat does brute force to crack WPA/WPA2 passwords at a speed of 31550 H/s, and Pyrit calculates hashes at a speed of 38000-40000 PMKs. Further verification of handshakes takes less than a second. From this it can be seen that even when checking one handshake, we increase the speed by about a third, and if we want to check several handshakes for one AP, then with oclHashcat we need to start all over again. In Pyrit, each new handshake takes a split second.
In order for Pyrit to unleash its full power, you must have proprietary video card drivers installed. Look at the article “” and the material referenced in it - it tells you step by step about installing drivers and Pyrit in Kali Linux 2 on a computer with a graphics card from AMD. You need to follow all the steps, not just the last instruction. I don't have an NVidia computer, so I don't have up-to-date instructions on installing the driver and Pyrit for NVidia systems.
The fastest cracking of WPA/WPA2 passwords
My initial data:
- attacked TD - DANIELLE2015
- the file with the pre-captured handshake is called DANIELLE2015-01.cap
Dictionary for cracking WPA/WPA2
I'll be using the rockyou dictionary that comes with Kali Linux. This is quite enough for training, but for practical attacks I can recommend generated dictionaries of phone numbers, generated dictionaries for specific APs of the form AP_name+digits, which fill the passphrase up to eight characters.
Let's copy the best dictionary file to the root directory.
Cp /usr/share/wordlists/rockyou.txt.gz .
Let's unpack it.
Gunzip rockyou.txt.gz
Since the minimum WPA2 password is required to be 8 characters, let's parse the file to filter out any passwords that are less than 8 characters and more than 63 (actually, you can just skip this line, it's entirely up to you). So we will save this file as newrockyou.txt.
Cat rockyou.txt | sort | uniq | pw-inspector -m 8 -M 63 > newrockyou.txt
Let's see how many passwords this file contains:
Wc -l newrockyou.txt
It contains as many as 9606665 passwords.
The original file contains even more.
Wc -l rockyou.txt
There are 14344392 passwords. So, we've made this file shorter, which means we can test the AP in a shorter period of time.
Finally, let's rename this file to wpa.lst.
Mv newrockyou.txt wpa.lst
Creating an ESSID in the Pyrit database
Now we need to create an ESSID in the database Pyrit data
Pyrit -e DANIELLE2015 create_essid
NOTE: If there is a space in the AP name, for example “NetComm Wireless”, then your command will be something like this:
Pyrit -e "NetComm Wireless" create_essid
Awesome, we now have the ESSID added to the Pyrit database.
Importing a dictionary into Pyrit
Now that the ESSID has been added to the Pyrit database, let's import our password dictionary.
Use the following command to import the pre-built password dictionary wpa.lst into the Pyrit database.
Pyrit -i /root/wpa.lst import_passwords
Create tables in Pyrit using a batch process
It's easy, just type the following command
Pyrit batch
Since this operation is performed on a laptop, I have 38000-40000 PMKs. This is far from the limit - desktop computers with a good graphics card will help you significantly increase the speed of these calculations.
You have to be careful how big your dictionary file is and how HOT your CPU and GPU are. Use additional cooling to avoid damage.
Hacking process with Pyrit
We will use a handshake attack using a database of pre-computed hashes. Once we completed all the necessary preparation steps, launching the attack became quite easy. Just use the following command to start the hacking process.
Pyrit -r DANIELLE2015-01.cap attack_db
That's all. The entire process, including the preliminary calculation of hashes, took several minutes. It took less than a second to traverse the entire database table to retrieve the password, if it was in the dictionary. My speed reached 6322696 PMKs. This is by far the fastest.
This takes seconds - so it's always worth using if the password is not found.
Handshake attack with dictionary in Pyrit without using pre-computed tables
If you don't want to create a database, but want to tinker with the dictionary file directly (which is much slower), you can do the following
Pyrit -r DANIELLE2015-01.cap -i /root/wpa.lst attack_passthrough
How fast is this method? 17807 PMKs per second. Much slower for my taste.
Cleaning Pyrit and the database
Finally, if necessary, you can remove your essid and do a cleanup.
Pyrit -e DANIELLE2015 delete_essid
This will free up quite a bit of disk space.
About dictionaries for aircrack -ng.
The first thing you should know is that ABSOLUTELY ALL actions given in such articles are without a VERY good dictionary (for the utility aircrack including), in case of hacking password, which includes countless different password combinations , not more than rat race. So I warn you right away: all your manipulations may turn out to be meaningless if the user happens to use an arbitrary combination like:
... which is achieved simply by meaningless “knocking” of the user on the keyboard. The method discussed here for decrypting APs with encryption classes WEP, WPA, WPA2 is based on a brute force attack, that is, dictionary search. Unfortunately, this is the problem with such methods: dictionary must contain, among others, the password invented by the victim. What is the probability that the dictionary you download or compile will contain the combination presented above? The network mask is unknown, you will have to brute force it blindly.
Neither aircrack nor hackers are alive. The password, and not only for Wi-Fi, can be found out in other ways. Read and get acquainted:
Without any dictionary - no way. Alas and ah. I warn you in advance - avoid old foreign dictionaries dating back to 2010. There are plenty of them on the Internet, and they are equally useless, and you will understand this yourself. As for the author of the article, he was rarely let down by a single dictionary. The only problem for you is that the archive for the “dictionary” in txt format weighs about 14 GB. By the way, this is also a little. A cosmic number of keyboard combinations have been generated there, they are filtered by the most common ones; Maybe your password will appear. It would be superfluous to remind you that files of this size should be downloaded separately, not as part of other downloads and with the browsers closed. It would be a shame if, after a long time, when trying to open a password document, you encounter an opening error. You'll have to download it again...
So, I’ll explain the principle of operation. If other options are possible for WEP, there are a lot of utilities for cracking WEP passwords in Kali, then in the case of more powerful protection such as WPA2 (today the most common type of protection), only the option with a dictionary or brute force is possible (in our case, too). Hacking WiFi using airodump will be possible only this way and not otherwise. This is the only but significant disadvantage of the method. The same applies to other methods of brute force and substitution of a password existing in the dictionary.
“Official” dictionaries for aircrack
There are no basic requirements for them. View - Text Document, compiled according to the principle of 1 password in 1 line with line breaks. The presence of Latin letters in both cases, Arabic numerals and several symbols.
Dictionaries for aircrack – where to get them?
If you want to use ready-made dictionaries for aircrack, which do not have any advantages over more modern ones, then I will again refer you to the official website:
http://www.aircrack-ng.org/
on the page of which these same dictionaries for aircrack are ready for downloading in links to third-party resources. Anyway, take a closer look. One way or another, you will still visit this site, trying to find dictionaries for aircrack online.
Further. The network is full of other suitable dictionaries that duplicate each other. This is how a lot of “hackers” work: someone else’s renamed it, God willing, they diluted it with their own, packaged it up, and it’s done. No one is immune from this. So you'll have to search.
The next problem with foreign dictionaries: the highest quality ones are compiled using the method “what passwords were found out, they were added to the list.” There is only one problem for us - in Russia, passwords are usually created differently. So even the best dictionary of keys worth 300 million may well “refuse” you after 9-12 hours of waiting.
The main problem, as already mentioned, is the size of the dictionaries. There are real masterpieces on the Internet. Almost all of them are from overseas. However, even psychologists and other specialists took part in their construction (according to the authors), trying to reproduce the most common random sets of symbols like “monkeys on the piano”. After all, the best password to come up with is:
- open Notepad
- close eyes
- hit the keyboard with all 10 fingers at once
- dilute the password with symbols like @, #, $, etc., adding an uppercase letter at the end. This is not “qwerty” for you...
- copy the result and use it as a password. You won’t be able to remember it, but it will take a hacker 150 years to hack it.
Make your own dictionaries for aircrack.
I'll be brief. Let's use the utility included in Kali Crunch. Designed to generate random passwords, it has a number of useful settings. Some of them are very useful if, for example, you manage to see part of the victim's password. That is, you know some of the symbols.
The generation process is simple. Launch a terminal and enter a command in the format:
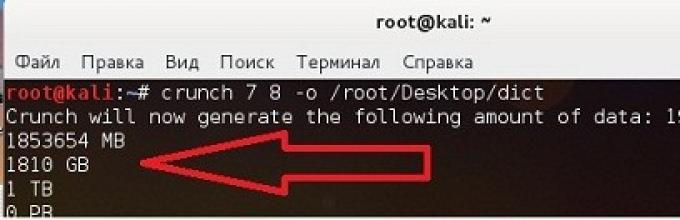
crunch 7 8 -o /root/Desktop/dictThe command will create a dictionary with the name dict on the Desktop from all sorts of alphanumeric combinations, containing from 7 to 8 characters - a regular password. Convenient, right? And you don’t need to download any dictionaries for aircrack... If you rejoice early, take a closer look at the size:

Yes, yes, quite a bit - about 2 Terabytes. Pichalka (...
What to do? You can add commands to make passwords more specific if you have a reason to do so. So, the generation command can take the form:
crunch 7 8 9876543210 -o /root/Desktop/dict.lstWhere 9876543210 – precisely and only symbols that appear in the future dictionary. And no more. Or:

In this case Crunch will create a dictionary with passwords #$ .
Many such dictionaries can be compiled, believe me, sometimes this method works very well. They will not weigh so much, they will be mobile, and they can be easily stored on external media. So, in the password selection command you can then specify the passwords you created, separated by commas (if homemade dictionaries for aircrack are stored on the Kali desktop):
aircrack-ng /root/filename.cap -w /root/Desktop/dict1,dict2,dict3BUT again
Using programs like Crunch or John The Riper not exactly an option that would be useful to a professional burglar. There are several reasons for this. I couldn’t manage to modify the script in any way so that it would be possible to split the process of cracking a password combination into several stages (meaning from session to session, from one reboot to another). This means that the hacking process can take months. Against the background of a sharp drop in computer performance (I think by half). And, in the end, as an option - a separate machine for brute force? An unaffordable luxury, in general. Working with a DUAL video card in 64-bit Windows 7 brought me the most effective results. The process is described in the article.
Dictionaries for aircrack – online services.
It would be strange if such a person did not appear. However, a service that includes selecting passwords using a dictionary has already existed for 3-4 years. It is located at:

It boasts of the shortest password decryption time and a dictionary of 600 million keys. I don’t know any reviews about it because I haven’t used it. Why? 17 US dollars per key (at the time of writing), however. You will need everything the same as in the case of selection using an available dictionary: you need to enter the BSSID of the victim, indicate the path to .cap file and finally an email address. As I assume, they will first send you a response about whether everything went well or not, and they will ask you to pay. How, when, I don’t know.
ATTENTION . Proceed at your own risk. If I were the creators of the resource, I would not be able to resist and deceive anyone who wanted to transfer me money just like that... But I repeat: I don’t know, I haven’t used it. In any case, the link to this one is defined by many search engines as malicious. I had to delete it, but the address is clearly visible in the site header in the picture. Who will use it - unsubscribe
So, the best dictionary is not a panacea. We use another method: .
Read: 6,338
Hello! This will be a companion article to my main series on wireless network security. I will dedicate it to a selection of Wi-Fi password databases. Only the most useful, without excess water.
You may disagree with my opinion on many points - comments are always open for discussion. Helping each other is encouraged.
This article has been prepared solely for the purpose of improving personal skills information security. The WiFiGid project is categorically against the use of information on other people's networks without obtaining the prior consent of their owners. Let's live together and not harm other people!
Layer of theory for introduction
The bases themselves will be lower. Here I couldn’t resist and will try to identify the existing problems in Wi-Fi brute methods. What approaches exist in this direction:
- Classic brute force on the fly – i.e. trying to connect to access points and immediately check passwords. The method has sunk into oblivion, do not use this anachronism!
- Intercepting a handshake and brute it using Aircrack - Hashcat - is the most effective technique that allows you to use all the power of your computer. I hope that is what you came here for.
- Brute WPS also has its place, but the second method is used more often.
What idea is important to us regarding the second point of the task:
There are passwords different lengths. Don't use bases without thinking about their purpose.
Here are some of my thoughts:
- Starting with WPA, there are no passwords shorter than 8 characters. Those. Anything below does not make sense to use. Of course, if you are unlucky to find a WEP network.
- People very often use numbers – phone numbers and dates – in their passwords.
- You can find popular leaked passwords, for example, from emails - home passwords to access points will also match. That is, it makes sense to run through popular lists of passwords (of course, longer than 8 characters).
- And if nothing else helps, you can use a complete search. There are already ready-made databases, but I prefer to use the Crunch generator - you set any conditions YOU NEED, and you get a ready-made database.
When using a head, the probability of successfully guessing a password increases exponentially.
Current databases
Now that we've sorted out the theory, it's time to provide ready-made bases. If you have something of your own, post it in the comments with explanations. Comments are being moderated, not everything will pass, trash is not needed here.
What is accessible and usable, the most popular password dictionaries in Russia and the CIS (dic and txt format - all text files):
- TOP Wi-Fi passwords for WPA, WPA2, WPA3
- TOP 9 million
- List of passwords E-mail
- Dates and birthdays
- Phones – Russia – Ukraine – Belarus
- 8 digit numbers
- 9 digit numbers
Alternatives
Here I will leave several alternative options for selecting passwords. What if the reader finds it useful:
- You can use generation programs - Crunch and John the Riper - which allows you to create databases for your specific ideas. But as a rule, sorting through continuous generics, even on state-of-the-art hardware, takes a very long time.
- There are online services (I don’t, because there are also villains) that have already deciphered many handshakes or will take on decrypting them - obviously this comes at a cost, but sometimes it’s worth it.
Kali Dictionaries
These hacking dictionaries are already present in any Kali Linux user. So feel free to use it and don’t download anything. Below I will give a list with a little explanation. But what was above is quite enough for normal work with varying degrees of success.
- RockYou (/usr/share/wordlists/rockyou) is the most popular dictionary for pentesting for any purpose. It can also be used for Wi-Fi, but I recommend first clearing inappropriate passwords through the same pw-inspector.
That's all. If you have anything to suggest, please leave it in the comments below. Let's see, we'll figure it out, but without the trash.